Reduce the threat of a hacker
Stop cybercriminals from hacking your computers and mobile devices and keep your sensitive information secure. We protect all endpoints from eavesdropping spyware.
How Does Anti-Keylogger, Keystroke Encryption Work?
Privacy & Data Protection for Desktop Computers and Laptops
Works on both PC and MacOS
Outsmart cybercriminals
Protect your keystroke data at the point of origin – the keyboard – and deliver it safely and securely into the application or browser.
A new path to foiling cybercriminals
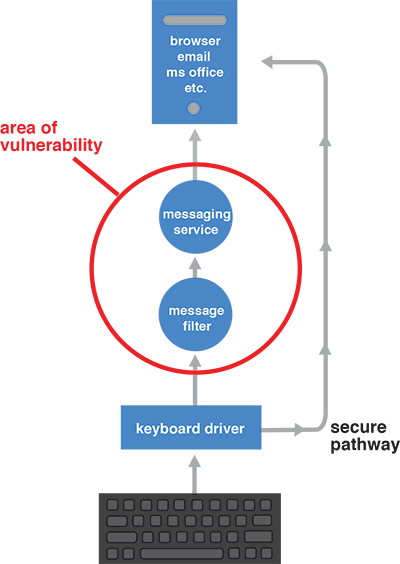
Our keystroke protection stops malicious spyware and malware programs by encrypting keystroke data and routing it directly to your internet browser or desktop through a secure pathway that’s invisible to the keyloggers.
Traditional keystroke data flows through a series of steps before it appears on your monitor, similar to running a relay race. Hidden in these steps is an area of vulnerability where cyber criminals try to take advantage using keylogger spyware.
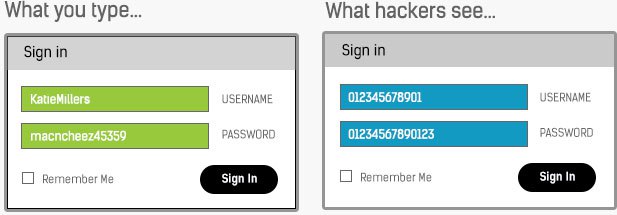
We bypass the places keyloggers can reside, helping to eliminate your vulnerability to attack. As a second level of security, we protect the pathway it creates with a military-grade 256-bit encryption code. At the same time, we send out a sequence of meaningless numbers in place of keystrokes, making any data collected by hackers completely meaningless.
Key Features
- Anti-Keylogger, Keystroke EncryptionControls your keyboard at the lowest layer in the kernel to guard against existing and new, “zero day” keyloggers.
- Anti-Screen CapturePrevents malware from secretly taking screenshots of your personal information or content displayed on your screen.
- Anti-ClickjackingDetect and highlight hidden clickjacking attacks to warn you from clicking on malicious invisible objects embedded in legitimate web pages
- CryptoColor®Visual verification shows you that GuardedID® is protecting your input by highlighting what you type in a color you select. (Currently available for Internet Explorer and Chrome, and coming soon for other browsers.)
- Malicious Driver MonitoringWorks as a constant anti-subversive service, detecting untrusted drivers, such as keyloggers, and displaying a warning containing the name of any suspect driver.
- Full ProtectionIncludes USB, Wireless & Bluetooth keyboards; Can also encrypt all international keyboards.